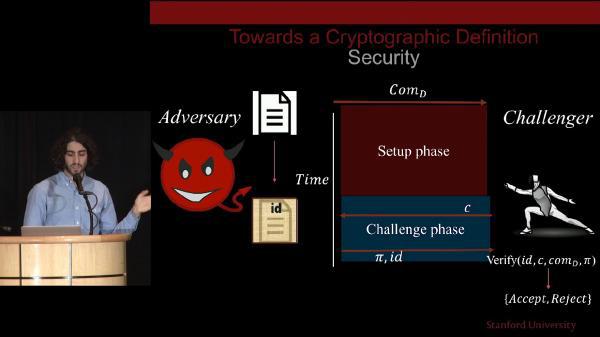
Modern cryptography plays an integral role in every aspect of online and electronic security, including providing evidence you’re speaking to the intended party and hindering spying on the subsequent communication. Cutting-edge cryptography tools will allow the creation of incredibly strong evidence that general information processing has been performed in a privacy-preserving and trustless way.